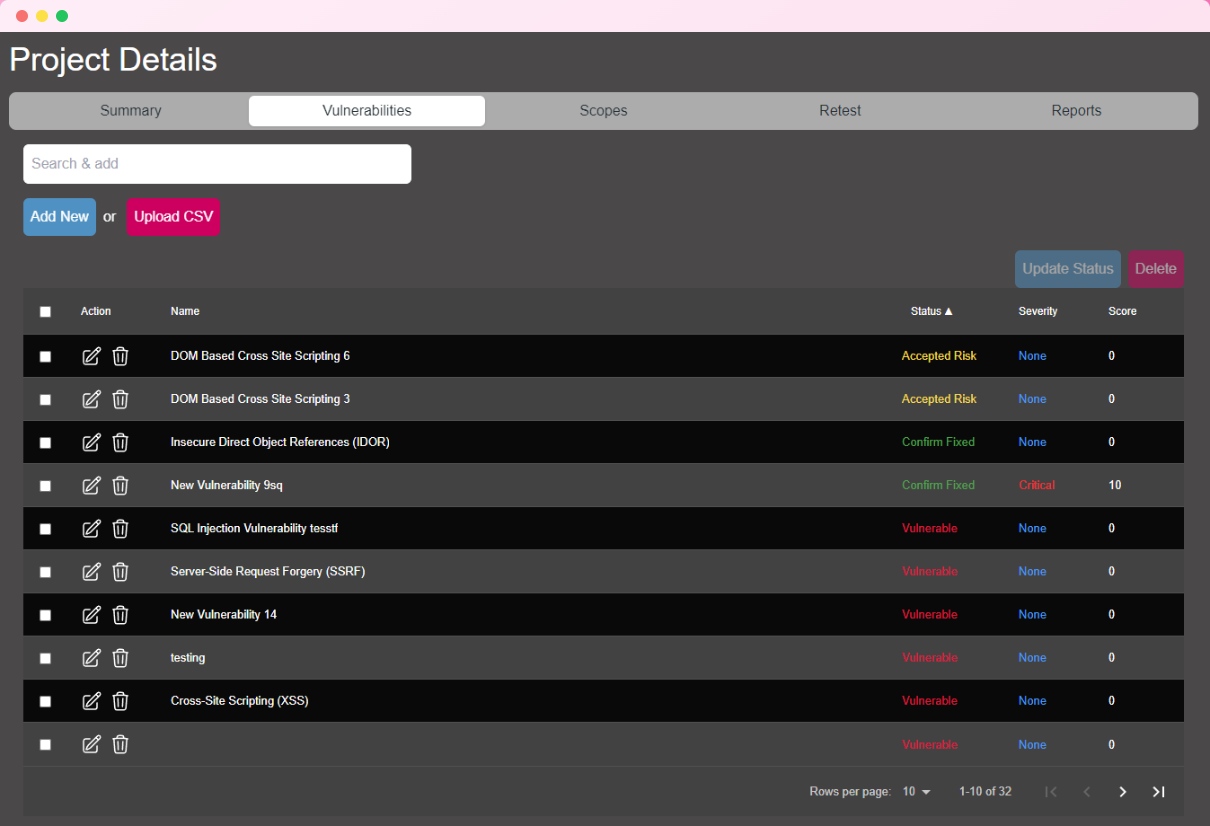
Project Vulnerabilities
Project vulnerabilities represent security issues found during assessments. Each vulnerability includes details like description, solution, and CVSS score.
Adding Vulnerabilities
Three ways to add vulnerabilities:
- Search Template: Find and import from Vulnerability Database
- Add New: Create blank vulnerability entry
- Upload CSV: Import from Nessus or compatible scan files
Validation Rules
- Cannot add vulnerabilities to completed projects
- Project must have defined scope in Project Scope tab
- Only active projects (Upcoming, In Progress, Delayed, On Hold) accept new vulnerabilities
Publishing Vulnerabilities
- Toggle vulnerabilities between published/unpublished state
- Only published vulnerabilities appear in customer dashboard
- Unpublished vulnerabilities remain visible only to internal users
- Use for reviewing findings before sharing with customers
CSV Import
Required columns for CSV import:
- Host: IP address or URL
- Port: Network port
- Name: Vulnerability title
- Description: Details about the issue
- Solution: Remediation steps
- Risk: Severity level (Critical, High, Medium, Low, Info)
Vulnerability Status
Three possible statuses:
- Vulnerable: Unresolved issue
- Confirmed Fix: Issue resolved
- Accepted Risk: Issue acknowledged as acceptable risk
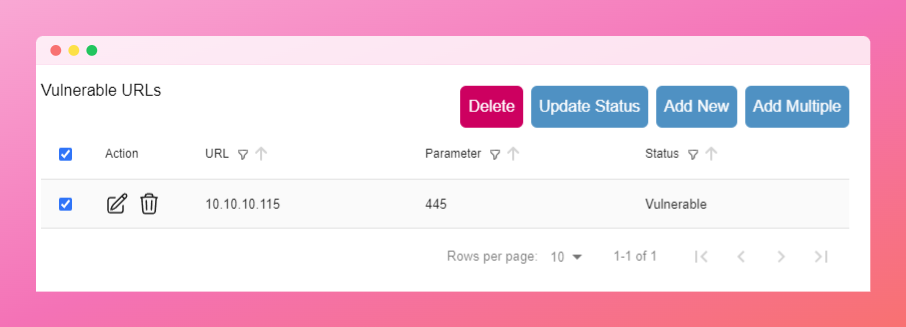
Vulnerability Instances
Each vulnerability requires at least one instance with:
- Specific location (URL, parameter, IP, port)
- Individual status tracking
- Independent verification